This chapter describes the access rules that govern Trusted IRIX/CMW. It includes a step-by-step description of how to log in, a discussion about dealing with the password mechanisms, an explanation of areas where Trusted IRIX/CMW differs from standard IRIX, and short descriptions of some day-to-day tasks that users of Trusted IRIX/CMW will need to perform. For a complete new-user tutorial on all aspects of the IRIX system, refer to your standard IRIX documentation.
The following sections are included:
Generally, the IRIX interactive desktop behaves in the same manner on a Trusted IRIX/CMW system as it does on a standard IRIX system. The most significant differences are a consequence of the Trusted IRIX/CMW security policies and are described in this section. This section does not describe how to use the desktop; for more information on the desktop see the Desktop User's Guide.
All windows on a Trusted IRIX/CMW system include an additional title bar, which displays the window's Mandatory Access Control (MAC) label. This is shown in Figure 3-1. This is the MAC label for the window's process, which is the same label as that for the shell in the case of an xterm or similar terminal window.
The window manager and X server prevent you from copying and pasting text from one window to another if the destination window's label does not dominate the originating window's label. For example, text from a more sensitive window may not be cut and pasted to a window with a less sensitive label. Therefore, the MAC policy of Trusted IRIX/CMW is also enforced by the window manager.
The trusted path window is always displayed on a Trusted IRIX/CMW system, including during system login (as discussed in “Logging In Using the CMW Dialog”). This window gives you greater control over the trusted behavior of the window manager. The trusted path is a subject that has the CAP_XTCB capability, so the primary purpose of the trusted path window is to inform you when you are and are not using a trusted subject.
The trusted path window is not a separate process but an integral part of the window manager. The window may not be lowered, iconified, or obscured by any other window. This is enforced by the window manager so that you are always aware of the current window manager behavior.
The window has two buttons, which by default are labeled “Trusted Path is Off” and “OpenGL Disallowed.” These buttons can be used to restrict or relax the policy of which windows can be displayed and used.
Below the buttons is a single bar displaying the label of the window that the mouse is positioned over. If the mouse is not positioned over any windows, the text changes to show “Background.” You can use this bar to determine the label of the current window if it becomes obscured.
Another long horizontal bar will appear at the bottom of the window when the mouse is positioned over a trusted window and the trusted path button is turned on. The bar will display “You Are On The Trusted Path.” This bar will also appear when the mouse is moved over the trusted path window, no matter what the state of the trusted path button.
The trusted path button can be used to force the window manager to restrict access to windows running with the CAP_XTCB capability. By default, this behavior is turned off, but when the button is clicked, the text will change to display “Trusted Path Is On” and only the trusted windows (that is, the windows with the CAP_XTCB capability) can be accessed. The mouse will not focus on a window that does not have this capability.
This behavior also prevents restricted windows from being displayed. For example, any process attempting to create a window without this capability will be blocked from displaying the window. As soon as the behavior is turned off (by clicking the button) all new windows that were blocked will be displayed.
When the trusted path is enforced, some window manager operations are still allowed on restricted windows, including iconifying, lowering, raising, and resizing windows. However, the window manager will prevent the contents of those windows from being updated.
The graphics hardware registers that are used by OpenGL applications are accessible to other processes. Therefore, it is possible for another process to capture the contents of the screen regardless of MAC label controls or capabilities.
On a Trusted IRIX/CMW system, by default, Open GL applications may not be displayed. Given that a large number of applications on this platform use Open GL, this behavior may be controlled by selecting the “OpenGL Disallowed” button, which will change the button to display “OpenGL Allowed.” Any OpenGL application running at the same MAC label of the user when they logged in may now be displayed. This behavior can be removed by clicking the “OpenGL Allowed” button.
The following applications behave differently on a Trusted IRIX/CMW system:
| Toolchest | The system administration tools that are accessible from the toolchest have not been customized for a Trusted IRIX/CMW system and, generally, will not behave correctly. System administration functions should be performed by editing the relevant configuration files or running the appropriate command-line tools. | |
| Icon catalog | The icon catalog and many other desktop functions will not work in a Trusted IRIX/CMW environment because of their dependence on the File Alteration Monitor (fam). fam is restricted from running on a Trusted IRIX/CMW system. For more information about fam, see the fam(1) man page. | |
| X applications | X applications should behave normally on a Trusted IRIX/CMW system within the constraints of the window manager and network security policies. | |
| IRIS GL applications | Applications that use the original GL graphics libraries may not be run on a Trusted IRIX/CMW system without the appropriate capabilities because the system cannot restrict the graphics to a specific MAC label. | |
| OpenGL applications | OpenGL applications are restricted by the “OpenGL Allowed” button. For more information see “OpenGL Allowed Button”. |
When no one is logged in to a Trusted IRIX/CMW machine, the system displays a login prompt and waits for a user to enter a login name. To log in, you must first have an account created for you on the system. Your system administrator should create this account for you and tell you the login name you are to use. If you are allowed to select your own login name, select a name that is easy to remember, such as your first name and the initial of your last name. When your account is created, a password may also be logged for you at that time by the system administrator. If so, you should know the password before you attempt to log in. If a password is not logged for you when your account is created, you should select one when you first log in.
When you are certain that the account has been created for you, you are ready to log in. When no one is logged in at the console, a window is displayed for the login dialog. Follow these instructions to log in:
The trusted path window is displayed on the screen, as shown in Figure 3-2, and the trusted path should be initialized “on.”
If the trusted path is not on, move the mouse cursor to the “Trusted Path Is Off” button and click. If the trusted path window does not indicate that the trusted path is on, call your system administrator.
Move the pointer to the CMW Login Dialog window. The trusted path window should state that “You Are On The Trusted Path.” Again, if it does not state that you are on the trusted path, call your system administrator.
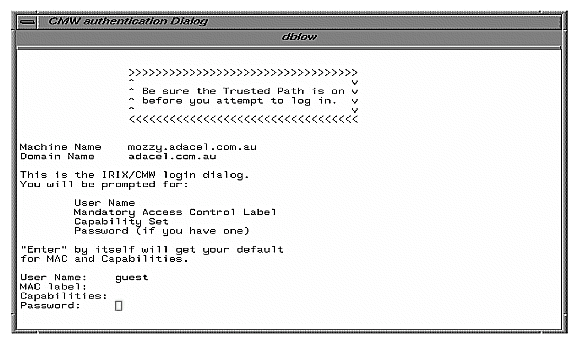
On the CMW Login Dialog window, you should see the User Name: prompt, as shown in Figure 3-3:
Enter the desired account name. You must enter an account name; there is no default.
You are prompted for a MAC label:
MAC Label:
If you do not enter a MAC label name (that is, if you simply press the Enter key) you are given your default login label.
You are prompted for a capability set:
Capabilities:
If you do not enter a capability set (that is, if you simply press the Enter key) you are given your default capability set.
You are prompted for your password:
Password:
Your password is not displayed as you type it in. Press the Enter key when you have typed your password.
If all responses were valid, you are logged in. The screen clears and the default windows and icons are displayed. The login process is now complete.
To log out of a Trusted IRIX/CMW system using the GUI, follow these steps:
Right click on the screen background and select the “Log Out” option. A confirmation pop-up window will appear.
In the confirmation window, click “Yes” to confirm the logout or “No” to cancel the logout process.
At times you may need to log in to a Trusted IRIX/CMW machine when you do not have access to the graphical login program. You can use Telnet sessions and serial terminals to log in to a Trusted IRIX machine.
The Trusted IRIX TTY login appears the same as a typical IRIX console login, but it does not prompt you for a MAC label or capabilities. You can specify a MAC label or capability on the login line in addition to your user ID. A TTY device may be configured to have a restricted MAC range, thereby limiting users to labels within that range. By default, a serial console will allow all labels. A MAC label specification is ignored for Telnet sessions.
To specify a MAC label, add a MAC= label, as follows:
login: root MAC=dblow Password: |
To specify a capability set, add a CAP= capability set, as follows:
login: root CAP=CAP_FOWNER,CAP_KILL+eip Password: |
You can specify both a MAC label and capability set, as follows:
login: user CAP=all+eip MAC=userlow Password: |
A login attempt will fail if you request a capability that does not exist or is not in your capability set, or you attempt to log in with a MAC label not in your clearance or not allowed by the TTY device.
It is possible for you (or one of your programs) to determine the current operating system environment you are in by using one of the methods described in this section.
To determine the identity and security features of your operating system, you can execute the sysconf command at a shell prompt. A complete description of all sysconf command options can be found in the sysconf(1) man page.
You will see a great deal of output and, towards the bottom of the list, the relevant information in the following format:
PROCESSORS R4000 2.2 AVAIL_PROCESSORS 1 SYSNAME IRIX HOSTNAME bandicoot RELEASE 6.5- ALPHA-1276144020 VERSION 01050909 MACHINE IP22 ARCHITECTURE mips HW_SERIAL 1762094967 HW_PROVIDER sgi ACL 1 AUDIT 1 CAP 2 INF 0 IP_SECOPTS 1 MAC 1 |
Passwords are the first line of defense of a trusted system. As a user, it is your responsibility to protect the privacy of your password at all times. Follow these rules regarding your password:
Never give your password to another user or allow another user to “borrow” your account.
Never keep your password written down anywhere near your machine.
Always commit your password to memory. If you forget it, the system administrator can change it for you.
Trusted IRIX/CMW contains facilities to generate passwords for users, however, these facilities are not configured to work by default. For more information about password generation see the passwd(1) man page. If your site is configured to allow you to select your own passwords, follow these rules when choosing your password:
Never choose a password that could be guessed by someone who knew personal information about you. For example, if someone stole your wallet with the intent of finding out information about you, make certain that your password is not related to something someone might find in your personal information, such as variations on your name or the name of a friend or family member.
Always use a random mix of printable characters, control characters, punctuation marks, and numerals when selecting a password.
Each password must have at least six characters. However, only the first eight characters are significant.
The password must contain at least two alphabet characters and one numeral character.
The password must not be related to the user's login name. Any reversing or circular shift of the characters in the login name will not be allowed. Capital letters are assumed to be equivalent to their lowercase counterparts.
The password must have at least three characters different from the previous password. Capital letters are assumed to be equivalent to their lowercase counterparts.
Trusted IRIX/CMW supports facilities to manage the lifetime of a password, also known as password aging. For more information about password aging see the passwd(1) man page and the IRIX Admin: Backup, Security, and Accounting guide.