This user's guide has been designed to introduce you to working with secure systems, and in particular with the SGI Trusted IRIX/CMW (Compartmented Mode Workstation) system. This guide provides information on how to maintain system integrity by using security features. It also describes the various modifications and additions made to standard IRIX that make this system secure.
This chapter introduces you to the basic concepts, terms, and features of a trusted system, and explains security procedures and mechanisms. It includes the following sections:
This section introduces you to the basic concepts, terms, and security procedures and mechanisms of a trusted system.
Operating systems that attempt to provide a secure environment for the development and storage of sensitive information are known as trusted systems. In an abstract sense, no system is ever perfectly secure from harm, so we use the term trusted rather than secure. A trusted system can be thought of as any system that fits the following criteria:
The system allows all users to do their ordinary and necessary work without difficulty.
The system enforces the security policy deemed by the management to be appropriate to the site.
The first criterion is the most important. If users are unable to do their ordinary and necessary work, they either will circumvent the security measures or they will not use the system at all. In either case, the trusted system is rendered useless. Many users are concerned that they will not be able to do their work in a trusted environment. A good site administration plan structures a trusted system so that the user is relatively unaffected by its functioning. Ideally, users should be able to perform all their tasks and only see the trusted features of the operating system when necessary.
The second criterion requires that the system have adequate security features to enforce the site security policy set forth by the management. Trusted IRIX/CMW offers a variety of security measures that are sufficient to satisfy most sites. These measures are as follows:
| Access Control Lists | An Access Control List (ACL) allows the owner of a file or directory to make a specific list of users and user groups and the specific permissions each one is allowed to the file or directory. ACLs are a standard feature of IRIX. | |
| Auditing | The audit subsystem allows the system administrator to keep a precise log of all system activity. Auditing is a standard feature of IRIX. | |
| Capability | A capability is a discreet unit of privilege that can be assigned to a process and allows the process to override a set of related system restrictions. | |
| Capability-based Privilege Mechanism | This is the mechanism through which a privilege is determined based on the set of effective capabilities in a process. Also, it is the mechanism through which capabilities are assigned to a process or an executable file, and through which a process manages its capabilities. | |
| Discretionary Access Control | Discretionary Access Control (DAC) is the standard IRIX system of file and directory permissions. | |
| Identification and Authentication | Trusted IRIX/CMW has improved user identification and authentication facilities that ensure the integrity of system passwords and help to ensure that only authorized users are granted access to the system. | |
| Mandatory Access Control | The Mandatory Access Control (MAC) facility allows the system administrator to assign security classification labels to files and directories and security clearance labels to users. This is in addition to the Access Control Lists, Capabilities, and Discretionary Access Controls available on the system. | |
| Mandatory Integrity | This is a part of the Mandatory Access Control system that covers an integrity requirement. It allows the system administrator to limit the ability of highly trusted users to access files and programs that are not absolutely secure and trusted. | |
| Mandatory Sensitivity | This is a part of Mandatory Access Control that allows the system administrator to restrict access to files, directories, and programs according to security clearance requirements. | |
| Privileges | Privilege is the ability to override system restrictions. This ability is based on an authority that is specific to the privilege mechanism or mechanisms in use by a given site. | |
| Superuser-based Privilege Mechanism | This is the mechanism through which the IRIX system associates privilege with the root user identity. |
The Trusted IRIX/CMW system is designed to address the three fundamental issues of computer security: policy, accountability, and assurance. By fully addressing these areas, the system becomes a trustworthy base for secure development and business. Because the nature of a trusted system is already constrained, little must be trusted beyond the system itself. When you run your application programs on the system, you have a reasonable certainty that your applications will be free from corruption and safe from intruders.
CMW stands for Compartmented Mode Workstation, which means that your individual windows and processes running simultaneously need not all be at the same MAC label. This “compartmentalization” of windows and processes adds greatly to the usability of the system. In all other ways, the system conforms to standard Trusted Computer System Evaluation Criteria (TCSEC) B3 feature set, but with assurance of security at the B1 level.
The most important security aspect of the system is a clear definition of the site security policy with respect to all the trusted system features listed in “What Is a Trusted System”. To accomplish this, all system objects have been examined and altered to close potential security holes and determine a basic clearance level. This examination and revision process ensures the integrity and security of the distributed system.
Another highly important security aspect is assurance. A secure system design must be inspected and approved by a competent agency. Trusted IRIX/CMW supports all security requirements for B1 assurance and CMW systems as set forth by the National Computer Security Center (NCSC) and all feature requirements through the TCSEC B3 level.
Trusted IRIX/CMW is a significant improvement over conventional trusted operating systems derived from the standard UNIX kernel. While secure operating systems necessarily compartmentalize user interactions, the system need not be hostile to experienced or novice users.
Trusted IRIX/CMW is fully integrated with standard IRIX. IRIX is the SGI implementation of the UNIX System V Operating System. Trusted IRIX/CMW is an add-on, developed to conform to the functional requirements set forth in the U.S. National Computer Security Center (NCSC) Orange Book for an A1-level trusted operating system. The Orange Book is a common name for the 5200.28-STD Department of Defense (DoD) Trusted Computer Systems Evaluation Criteria. Trusted IRIX/CMW will be evaluated at the assurance level as a B1 system.
As a modified version of an existing operating system, many of the underlying features of Trusted IRIX/CMW have withstood the test of time. Designing a system that promoted ease of use was a paramount consideration in the creation of IRIX. SGI has a firm commitment to visual computing, evidenced in the graphical tools provided to you in the IRIX environment.
Part of our commitment to ease of use is our commitment to user-friendliness. A consistent and logical framework underlies the design of SGI visual desktop tools.
SGI consistently ranks at the top or near the top in customer satisfaction polls. Customer support, in a timely manner, has and will continue to be a corporate goal.
Customers in the United States may contact SGI customer support at 1-800-800-4SGI. Customers outside the United States may contact their local SGI service representative
The distinguishing difference between trusted systems and nontrusted systems is the security-enhanced feature set. For CMW-level systems, this feature set includes four main components. These components are improved identification and authentication of users, auditing, object reuse, and access control (MAC and DAC).
As well as the required feature set, SGI has implemented the X Window System and networking services for the trusted environment. Each component feature is described in detail in this section.
Every trusted system has a Trusted Computing Base (TCB). The TCB is the system hardware, the operating system program itself, and the commands, utilities, tools, and system files that are known to be secure. This set of hardware, files, and programs is the trusted part of a trusted system.
Within the TCB, there are subjects and objects. A subject is any active force on the system, such as a user's shell process, or the audit daemon, or the operating system itself. An object is any passive resource on the system, such as a text file, a page of memory, or a piece of system hardware.
Trusted IRIX/CMW is fully configurable to your site's needs. You are free to select your own security clearances, your own capabilities and access control lists, and your own system of password protection.
The Identification and Authentication (I&A) mechanism controls user access to the system. In common terms, the I&A mechanism is the login procedure. This subsystem is always active if the system is running, and it is impossible to have any contact with the system without first logging in through the I&A system.
The improved I&A facilities of Trusted IRIX/CMW allow the administrator to be certain that the people on the system are authorized users and that private password integrity is maintained to the highest possible levels.
Under Trusted IRIX/CMW, encrypted passwords are stored separately from other user identification information. This separate location is hidden from normal user access, so the process of a systematic dictionary encryption hunt for a password is precluded. User clearance information is also stored in a hidden or shadow file. Under Trusted IRIX/CMW, the /etc/passwd file does not contain the encrypted password; only the shadow password file contains that information.
In response to extensions to the CMW requirements, passwords can be generated automatically for the users under Trusted IRIX/CMW.The system administrator can configure the system to require this feature for every password change, or it can be an option for the user. System administrators can require passwords to be changed regularly.
Individual users may have a range of security levels available that have been predetermined by the administrator. The user is not always required to log in at the highest assigned level, thus allowing the flexibility to log in at a level appropriate for a given task. After a successful login has been established, the user may change the clearance of his or her process during the course of the login session. When this happens, all open file descriptors of the process are closed and all objects cleared to prevent declassification or violation of the security policy. All changes of clearance are audited.
Mandatory Access Control (MAC) allows the system administrator to set up policies and accounts that will allow each user to have full access to the files and resources he or she needs, but not to other information and resources not immediately necessary to perform assigned tasks. The access control is called mandatory because the system does not allow the owner of the files to change the security classification of system objects. Also, under MAC, access permission cannot be passed from one user to another, as under traditional UNIX systems, which use only Discretionary Access Control. Trusted IRIX/CMW includes both Mandatory and Discretionary Access Control, which work together to precisely control system access.
Under Trusted IRIX/CMW, MAC is divided into two interrelated subsystems: Mandatory Sensitivity and Mandatory Integrity. The access-control enhancements to Trusted IRIX/CMW allow the administrator to set up levels of clearance and related categories of files and other resources, and to assign each user a clearance (or range of clearances). Through this system of access controls, the administrator can custom tailor a user's environment so that the particular user has access only to those files and resources he or she needs to complete required tasks. If there is a breach into that user's account, the unauthorized user has access to very little of the site's protected information.
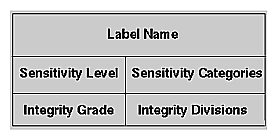
Each label used for access control has two parts: the sensitivity label and the integrity label. Figure 1-1 shows the components of a label.
Sensitivity labels define the secretness or classification of files and resources and the clearance level of users. A sensitivity label is composed of a sensitivity level and possibly some number of sensitivity categories.
There are 256 hierarchical sensitivity levels available for the administrator to create security classifications. In a commercial environment, this label attribute could be used to classify, for example, levels of a management hierarchy. Each file or program has one hierarchical sensitivity level. A user may be allowed to use several different levels, but only one level may be used at any given time.
Over 65,000 sensitivity categories are available for files and programs. For example, categories could include information sorted by subject matter such as geography, demography, astronomy, and others. Each file or user can be a member of any number of categories or of no categories.
While the sensitivity labels identify whether a user is cleared to view certain information, integrity labels identify whether data is reliable enough for a specific user to see. An integrity label is composed of an integrity grade and some number of integrity divisions.
There are 256 hierarchical grades to classify the reliability of information. For example, data could be classified as an unreliable rumor or as an absolute, confirmed fact.
There are over 65,000 divisions available to classify information based on its source. The source implies probable integrity of the data. For example, sources of data could be divided into Canadian Government, U.S. Government, CBS News, Hearst Publications, and others. In the commercial environment, data sources could be Trade Shows, Press Releases, Conversational, Dataquest, and the like.
Label names are configurable so that specific sites can control naming conventions to meet their special requirements. For example, the site administrator has control of name length (within limits) and could use non-English names, if desired.
Users should only use labels that have label name aliases associated with them. A user who wishes to use a label without a name should request the system administrator to add one. The non-aliased representation of labels can be both verbose and confusing, leading to possible mishandling by the unwary.
Trusted IRIX/CMW supports the POSIX P1003.1e Draft16 definition for Access Control Lists (ACLs). This draft standard provides for traditional file permission bits working in concert with the more versatile ACLs. Discretionary Access Control (DAC ) permissions are defined by the user who owns the file in question. For example, if a user has a personal file in his or her home directory, that user can set the DAC permissions to allow no other users on the system to view, copy, or edit that file. Default DAC permissions for newly created files are set via the umask command.
Thus, to gain access to a file that was created by another user, a user must not only have the proper MAC clearance, but must have set the DAC permissions on the file to allow others to access it. DAC permissions should be set in accordance with site security policies.
Default DAC permissions for newly created files depend on the umask and on any default ACL entries found in the containing directory.
A foundation of Trusted IRIX/CMW is the system audit trail. The system audit trail provides a means for the system administrator to oversee each important event taking place on the system. The audit trail is useful for tracking changes in sensitive files and programs and for identifying inappropriate use of the system.
The audit trail is generated by additional code in the operating system kernel that notes specific important events, such as file creation, file changes, file removal, invocation of programs, and the login and logout events.
The audit subsystem allows the administrator to create a dynamic record of the system's activity. This record allows the administrator to hold each user strictly accountable for his or her actions. The audit system is completely configurable at any time by the audit administrator.
Audit information must be carefully gathered and protected so that actions affecting security can be traced to the responsible party. Trusted IRIX/CMW records the occurrences of security-relevant events in an audit log. For each event audited, the system records the date and time of the event, the initiating user, the type of event, the success or failure of the event, and the name and security classification of the files or programs used.
The auditing process is transparent to the user. It is important to recognize that when you work on a trusted system, your actions will be audited. You should not, however, be fearful of the auditing process. Its function is to protect you from others who may try to use your user identity for mischief.
To preclude accidental disclosure of data, display memory and long-term data storage are subject to an object reuse policy and implementation. For example, all system memory is always automatically cleared before it is allocated to another program. Surrendered disk space is also cleaned before it is reallocated.
The purpose of trusted networking is to properly label data that is imported or exported from the system, and to appropriately enforce the system security policy on that data.
The Trusted Security Information Exchange (TSIX) standard was created to allow various trusted operating system vendors to interoperate. Under TSIX networking, labeling occurs at two levels. At the Network Level, IP Security Options (RIPSO or CIPSO) are used to route traffic. At the Session Manager Level, Security Attribute Modulation Protocol (SAMP) and Security Attribute Token Mapping Protocol (SATMP) are used to send all the Security Attributes required to enforce security policy between systems on the network.
You should contact your administrator to determine the level of networking support available at your site. Some sites may have a very open networking environment with full connection to Trusted IRIX/CMW machines, while others may not allow any connection between trusted and untrusted systems, or even between trusted systems. Your implementation will be unique, and can be explained to you by your administrator.
NCSC B-level security standards indicate that label information must be preserved when files are placed on magnetic storage media such as tapes. Trusted IRIX/CMW has modified the tar command to include the M keyword, to maintain label information on tape media.
Additionally, CMW standards specify that all paper output must be marked with the label of the information printed. Trusted IRIX/CMW line printer software has been modified to add this feature.