The terms listed in this glossary are used in the trusted systems community.
| *-property | A Bell-La Padula security model rule allowing a subject write access to an object only if the security level of the object dominates the security level of the subject. Also called confinement property. | |||
| acceptance inspection | The final inspection to determine whether or not a facility or system meets the specified technical and performance standards. This inspection is held immediately after facility and software testing and is the basis for commissioning or accepting the information system. | |||
| access | A specific type of interaction between a subject and an object that results in the flow of information from one to the other. | |||
| access control | The process of limiting access to the resources of a system only to authorized programs, processes, or other systems (in a network). See controlled access and limited access. | |||
| access control list | A discretionary access control entity associated with an object, consisting of a list of entries where each entry is an identifier (a user or group of users) coupled with a set of access permissions for that user or group. | |||
| access control mechanism | Hardware or software features, operating procedures, management procedures, and various combinations of these designed to detect and prevent unauthorized access and to permit authorized access in an automated system. | |||
| access level | The hierarchical portion of the security level used to identify the sensitivity of data and the clearance or authorization of users.
| |||
| access period | A segment of time, generally expressed on a daily or weekly basis, during which access rights prevail. | |||
| access port | A logical or physical identifier that a computer uses to distinguish different tty input/output data streams. | |||
| access type | The nature of an access right to a particular device, program, or file (for example, read, write, execute, append, modify, delete, or create). | |||
| accountability | The property that enables activities on a system to be traced to individuals who may then be held responsible for their actions. | |||
| add-on security | The retrofitting of protection mechanisms, implemented by hardware or software. | |||
| administrative security | The management constraints and supplemental controls established to provide an acceptable level of protection for data. Also called procedural security. | |||
| administrator | In the trusted system, the administrator is responsible for system administration tasks: filesystem maintenance and repair, account creation, and other miscellaneous administrative duties. | |||
| assurance | A measure of confidence that the security features and architecture of an AIS accurately mediate and enforce the security policy. | |||
| attack | The act of trying to bypass security controls on a system. An attack may be active, resulting in the alteration of data; or passive, resulting in the release of data.
| |||
| audit trail | A chronological record of system activities that is sufficient to enable the reconstruction, review, and examination of the sequence of environments and activities surrounding or leading to an operation, a procedure, or an event in a transaction from its start to final results. Alternatively, a set of records that collectively provide documentary evidence of processing used to aid in tracing from original transactions forward to related records and reports, or backwards from records and reports to their component source transactions. | |||
| auditor | The auditor is an administrator who maintains and examines the system audit trail. This person is responsible for maintaining and rearchiving the information, examining the records for abuse, and customizing the audit record gathering configuration. | |||
| authenticate | To verify the identity of a user, device, or other entity in a computer system, often as a prerequisite to allowing access to resources in a system. Alternatively, to verify the integrity of data that have been stored, transmitted, or otherwise exposed to possible unauthorized modification. Alternatively, to establish the validity of a claimed identity. | |||
| authentication | Verifying the claimed identity of a principal. | |||
| authenticator | The means used to confirm the identity or to verify the eligibility of a station, originator, or individual. Alternatively, a record containing information that can be shown to have been recently generated using the session key known only by the client and server. | |||
| authorization | The granting of access rights to a user, program, or process. Alternatively, the process of determining whether a client may use a service, which objects the client is allowed to access, and the type of access allowed for each. | |||
| availability of data | The state when data are in the place needed by the user, at the time the user needs them, and in the form needed by the user. | |||
| back door | See trap door. | |||
| backup plan | See contingency plan. | |||
| bandwidth | A characteristic of a communication channel that is the amount of information that can be passed through it in a given amount of time, usually expressed in bits per second. | |||
| Bell-LaPadula model | A formal state transition model of computer security policy that describes a set of access control rules. In this formal model, the entities in a computer system are divided into abstract sets of subjects and objects. The notion of a secure state is defined, and it is proven that each state transition preserves security by moving from secure state to secure state, thereby inductively proving that the system is secure. A system state is defined to be secure if the only permitted access modes of subjects to objects are in accordance with a specific security policy. In order to determine whether or not a specific access mode is allowed, the clearance of a subject is compared to the classification of the object, and a determination is made as to whether the subject is authorized for the specific access mode. See star property (*-property) and simple security property. | |||
| benign environment | A nonhostile environment that may be protected from external hostile elements by physical, personnel, and procedural security countermeasures. | |||
| between-the-lines entry | Unauthorized access obtained by tapping the temporarily inactive tty of a legitimate user. See piggyback. | |||
| beyond A1 | A level of trust defined by the DoD Trusted Computer System Evaluation Criteria (TCSEC) that is beyond the state-of-the-art technology available at the time the criteria were developed. It includes all A1-level features plus additional features not required at the A1 level. | |||
| browsing | The act of searching through storage to locate or acquire information without necessarily knowing of the existence or the format of the information being sought. | |||
| callback | A procedure for identifying a remote system. In a callback, the host system disconnects the caller and then dials the authorized telephone number of the remote system to reestablish the connection. Synonymous with dial back. | |||
| capability | A capability is a special privilege given to a process to override the system security policy. Each capability may have associated with it one or more flags. For processes, three flags are always associated with the capability, namely the effective, the permitted, and the inheritable flag. A file may have zero or more of these flags associated with it for a capability. Appropriate privilege is determined solely by a process having a specific capability's effective capability flag set. | |||
| category | The non-hierarchical component of the MSEN portion of a security label. That is, a logical division of information that spans hierarchical security levels as a means of increasing the protection of the data and further restricting access to the data. Typical examples would be Politics, Art, or Sports. There can be up to 65,536 different categories on your system. | |||
| certification | The technical evaluation of a system's security features that establishes the extent to which a particular computer system's design and implementation meet a set of specified security requirements. | |||
| channel | An information transfer path within a system. May also refer to the mechanism by which the path is affected. | |||
| ciphertext | The output of an encryption function. Encryption transforms plaintext into ciphertext. | |||
| clearance | A security clearance represents the combination of sensitivity level and categories that you are permitted to access. | |||
| client | A process that makes use of a network service, on behalf of a user. Note that in some cases a server may itself be a client of some other server (for example, a print server may be a client of a file server). | |||
| closed security environment | An environment in which both of the following conditions hold true: (1) Application developers (including maintainers) have sufficient clearances and authorizations to provide an acceptable presumption that they have not introduced malicious logic. (2) Configuration control provides sufficient assurance that applications and the equipment are protected against the introduction of malicious logic before and during the operation of system applications. | |||
| communications security | Measures taken to deny unauthorized persons information derived from telecommunications of the U.S. government concerning national security, and to ensure the authenticity of such telecommunications. Communications security includes cryptosecurity, transmission security, and physical security of communications security material and information. | |||
| compromise | A violation of the security policy of a system such that unauthorized disclosure of sensitive information may have occurred. | |||
| compromising emanations | Unintentional data-related or intelligence-bearing signals that, if intercepted and analyzed, disclose the information transmission received, handled, or otherwise processed by any information processing equipment. | |||
| computer abuse | The misuse, alteration, disruption or destruction of data processing resources. The key aspects are that it is intentional and improper. | |||
| computer cryptography | The use of a crypto-algorithm in a computer, microprocessor, or microcomputer to perform encryption or decryption in order to protect information or to authenticate users, sources, or information. | |||
| computer fraud | Computer-related crimes involving deliberate misrepresentation, alteration, or disclosure of data in order to obtain something of value (usually for monetary gain). A computer system must have been involved in the perpetration or cover-up of the act or series of acts. A computer system might have been involved through improper manipulation of input data; output or results; applications programs; data files; computer operations; communications; or computer hardware, systems software, or firmware. | |||
| COMSEC | Refers to communications security. | |||
| concealment system | A method of achieving confidentiality in which sensitive information is hidden by embedding it in irrelevant data. | |||
| confidentiality | The concept of holding sensitive data in confidence, limited to an appropriate set of individuals or organizations. | |||
| configuration control | The process of controlling modifications to the system's hardware, firmware, software, and documentation that provides sufficient assurance that the system is protected against the introduction of improper modifications before, during, and after system implementation. | |||
| configuration management | The management of security features and assurances through control of changes made to a system's hardware, software, firmware, documentation, test, test fixtures, and test documentation throughout the development and operational life of the system. | |||
| configuration range | The evaluation of a computer system by the NCSC (National Computer Security Center) is typically performed on a set of computer systems manufactured by the evaluatee rather than on just one particular computer system model. Due to the complexity of the evaluation process, it is common that only a closely related subset of the evaluatee's computer system product line be evaluated. The exact definition of the set of computer systems that is being evaluated is called the configuration range. The definition is exact. For example, part numbers of cables that connect keyboards to the system are part of the definition, and use of even a keyboard cable with a part number not in the configuration range will cause the evaluation not to be valid for that system. It is important to remember that the whole computer system is being evaluated, not just the software. | |||
| confinement | The prevention of the leaking of sensitive data from a program. | |||
| confinement channel | See covert channel. | |||
| contamination | The intermixing of data at different sensitivity and need-to-know levels. The lower-level data is said to be contaminated by the higher level data; thus, the contaminating (higher level) data may not receive the required level of protection. | |||
| contingency plan | A plan for emergency response, backup operations, and post-disaster recovery maintained by an activity as a part of its security program that ensures the availability of critical resources and facilitates the continuity of operations in an emergency situation. Also called disaster plan and emergency plan. | |||
| control zone | The space (expressed in feet of radius, surrounding equipment processing sensitive information) that is under sufficient physical and technical control to preclude an unauthorized entry or compromise. | |||
| controlled access | See access control. | |||
| controlled sharing | The condition that exists when access control is applied to all users and components of a system. | |||
| cost-risk analysis | The assessment of the costs of providing data protection for a system versus the cost of losing or compromising the data. | |||
| countermeasure | Any action, device, procedure, technique, or other measure that reduces the vulnerability of or threat to a system. | |||
| covert channel | A communications channel that allows two cooperating processes to transfer information in a manner that violates the system's security policy. Synonymous with confinement channel. Alternatively, a communication channel that allows a process to transfer information in a manner that violates the system's security policy. See also covert storage channel and covert timing channel. | |||
| covert storage channel | A covert channel that involves the direct or indirect writing of a storage location by one process and the direct or indirect reading of the storage location by another process. Covert storage channels typically involve a finite resource (for example, sectors on a disk) that is shared by two subjects at different security levels. | |||
| covert timing channel | A covert channel in which one process signals information to another by modulating its own use of system resources (for example, CPU time) in such a way that this manipulation affects the real response time observed by the second process. | |||
| crypto-algorithm | A well-defined procedure or sequence of rules or steps used to produce a key stream or cipher text from plain text and vice versa. | |||
| cryptography | The principles, means and methods for rendering information unintelligible, and for restoring encrypted information to intelligible form. | |||
| cryptosecurity | The security or protection resulting from the proper use of technically sound cryptosystems. | |||
| DAC | Discretionary Access Control. | |||
| data | Information with a specific physical representation. | |||
| data flow control | See information flow control. | |||
| data integrity | The requirement that data meet an a priori expectation of quality. Alternatively, the state that exists when computerized data is the same as that in the source documents and has not been exposed to accidental or malicious alteration or destruction. | |||
| data security | The protection of data from unauthorized (accidental or intentional) modification, destruction, or disclosure. | |||
| dedicated security mode | See modes of operation. | |||
| default classification | A temporary classification reflecting the highest classification being processed in a system. The default classification is included in the caution statement affixed to the object. | |||
| degauss | To reduce magnetic flux density to zero by applying a reverse magnetizing field. | |||
| degausser | An electrical device that can generate a magnetic field for the purpose of degaussing magnetic storage media. | |||
| Degausser Products List | A list of commercially produced degaussers that meet National Security Agency specifications. This list is included in the NSA Information Systems Security Products and Services Catalogue, and is available through the Government Printing Office. | |||
| denial of service | Any action or series of actions that prevent any part of a system from functioning in accordance with its intended purpose. This includes any action that causes unauthorized destruction, modification, or delay of service. Synonymous with interdiction. | |||
| dial back | See callback. | |||
| dial up | The service whereby a computer can use the telephone to initiate and effect communication with a computer. | |||
| disaster plan | See contingency plan. | |||
| Discretionary Access Control | A means of restricting access to objects based on the identity and the need of the user, process and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject. See also Mandatory Access Control. | |||
| division | The non-hierarchical component of the MINT part of the security label. This is the integrity part of the security label. The division component is very similar to the category component of the MSEN part of the security label. There can be up to 65,536 different divisions on your system. Typical examples of a division might be Prose, Poetry, Verse. | |||
| DoD Trusted Computer System Evaluation Criteria | A document published by the National Computer Security Center containing a uniform set of basic requirements and evaluation classes for assessing degrees of assurance in the effectiveness of hardware and software security controls built into systems. These criteria are intended for use in the design and evaluation of systems that process and store sensitive or classified data. This document is Government Standard DoD 5200.28-STD and is frequently referred to as “The Criteria” or “The Orange Book”. | |||
| domain | The unique context (for example, access control parameters) in which a program is operating; in effect, the set of objects that a subject has the ability to access. See process and subject. Alternatively, the set of objects that a subject has the ability to access. | |||
| dominate | Access to a file or resource under Mandatory Access Control is determined according to “domination.” You can view a file only if your process label dominates the label of the file. One label (high) dominates another label (low) if all four of the following conditions are true:
| |||
| emanations | See compromising emanations. | |||
| embedded system | A system that performs or controls a function, either in whole or in part, as an integral element of a larger system or subsystem. | |||
| emergency plan | See contingency plan. | |||
| emission security | The protection resulting from all measures taken to deny unauthorized persons information of value that might be derived from intercept and from an analysis of compromising emanations from systems. | |||
| end-to-end encryption | The protection of information passed in a telecommunications system by cryptographic means, from point of origin to point of destination. Alternatively, protection of traffic in a communications network by encrypting it at the source and decrypting it at the destination so that all nodes it passes through remain ignorant of its actual content. | |||
| entrapment | The deliberate planting of apparent flaws in a system for the purpose of detecting attempted penetrations. | |||
| environment | The aggregate of external procedures, conditions, and objects that affect the development, operation, and maintenance of a system. | |||
| EPL | The Evaluated Products List | |||
| erasure | A process by which a signal recorded on magnetic media is removed. Erasure is accomplished in two ways: (l) alternating current erasure, in which the information is destroyed by applying an alternating high and low magnetic field to the media; or (2) direct current erasure, in which the media are saturated by applying a unidirectional magnetic field. | |||
| Evaluated Products List | A list of equipments, hardware, software, and firmware that have been evaluated against and found to be technically compliant with, at a particular level of trust, the DoD TCSEC by the NCSC. The EPL is included in the National Security Agency Information Systems Security Products and Services Catalogue, which is available through the Government Printing Office. | |||
| evaluation criteria | Trusted IRIX/CMW meets the requirements specified for the Trusted Computer System Evaluation Criteria (TCSEC). The U.S. government specifies a set of criteria that trusted systems must meet to be evaluated successfully. A trusted system must offer a number of specific security features and must demonstrate that it can be maintained and distributed in a trusted fashion. | |||
| executive state | One of several states in which a system may operate and the only one in which certain privileged instructions may be executed. Such instructions cannot be executed when the system is operating in other (for example, user) states. Synonymous with supervisor state. | |||
| exploitable channel | Any information channel that is usable or detectable by subjects external to the trusted computing base whose purpose is to violate the security policy of the system. See also covert channel. Alternatively, any channel that is usable or detectable by subjects external to the Trusted Computing Base. | |||
| fail safe | Pertaining to the automatic protection of programs or processing systems to maintain safety when a hardware or software failure is detected in a system. | |||
| fail soft | Pertaining to the selective termination of affected nonessential processing when a hardware or software failure is detected in a system. | |||
| failure access | An unauthorized and usually inadvertent access to data resulting from a hardware or software failure in the system. | |||
| failure control | The methodology used to detect and provide fail-safe or fail-soft recovery from hardware and software failures in a system. | |||
| fault | A condition that causes a device or system component to fail to perform in a required manner. | |||
| fetch protection | A system-provided restriction to prevent a program from accessing data in another user's segment of storage. | |||
| file protection | The aggregate of all processes and procedures in a system designed to inhibit unauthorized access, contamination, or elimination of a file. | |||
| file security | The means by which access to computer files is limited to authorized users only. | |||
| flaw | An error of commission, omission, or oversight in a system that allows protection mechanisms to be bypassed. | |||
| flaw hypothesis methodology | A systems analysis and penetration technique in which specifications and documentation for the system are analyzed and flaws in the system are hypothesized. The list of hypothesized flaws is then prioritized on the basis of the estimated probability that a flaw exists and, assuming a flaw does exist, on the ease of exploiting it, and on the extent of control or compromise it would provide. The prioritized list is used to direct a penetration attack against the system. | |||
| formal access approval | Documented approval by a data owner to allow access to a particular category of information. | |||
| formal proof | A complete and convincing mathematical argument, presenting the full logical justification for each proof step, for the truth of a theorem or set of theorems. The formal verification process uses formal proofs to show the truth of certain properties of formal specification and for showing that computer programs satisfy their specifications. | |||
| formal security policy model | A mathematically precise statement of a security policy. To be precise, such a model must represent the initial state of a system, the way in which the system progresses from one state to another, and a definition of a secure state of the system. To be acceptable as a basis for a Trusted Computing Base, the model must be supported by a formal proof that if the initial state of the system satisfies the definition of a “secure” state and if all assumptions required by the model hold, then all future states of the system will be secure. Some formal modeling techniques include: state transition models, temporal logic models, denotational semantics models, algebraic specification models. An example is the model described by Bell and LaPadula in [Bell, D. E. and LaPadula, L. J. Secure Computer System: Unified Exposition and Multics Interpretation, MTR-2997 Rev. 1, MITRE Corp., Bedford, Mass., March 1976]. See also Bell-LaPadula model and security policy model. | |||
| formal verification | The process of using formal proofs to demonstrate the consistency between a formal specification of a system and a formal security policy model (design verification) or between the formal specification and its high-level program implementation (implementation verification). | |||
| front-end security filter | A security filter, which could be implemented in hardware or software, that is logically separated from the remainder of the system to protect the system's integrity. Alternatively, a process that is invoked to process data according to a specified security policy prior to releasing the data outside the processing environment or upon receiving data from an external source. | |||
| functional testing | The segment of security testing in which the advertised security features of the system are tested, under operational conditions, for correct operation. | |||
| grade | The hierarchical component of the MINT part of the security label. This is the representation of the integrity level of an object or the integrity requirement of a subject. The higher the value, the higher the integrity level or requirement. Typical examples of grade are as follows:
| |||
| granularity | An expression of the relative size of a data object; for example, protection at the file level is considered coarse granularity, whereas protection at field level is considered to be of a finer granularity. Alternatively, the relative fineness or coarseness by which a mechanism can be adjusted. The phrase “the granularity of a single user” means the access control mechanism can be adjusted to include or exclude any single user. | |||
| guard | A processor that provides a filter between two disparate systems operating at different security levels or between a user process and a database to filter out data that the user is not authorized to access. | |||
| handshaking procedure | A dialogue between two entities (for example, a user and a computer, a computer and another computer, or a program and another program) for the purpose of identifying and authenticating the entities to one another. | |||
| host to front-end protocol | A set of conventions governing the format and control of data that are passed from a host to a front-end machine. | |||
| I&A | Identification and Authentication. | |||
| identification | The process that enables recognition of an entity by a system, generally by the use of unique machine-readable user names. | |||
| Identification and Authentication | I&A is the process of determining (with some level of confidence) the true identity of a user. The identification process usually requires both a user name and a password. The authentication part of the process is the underlying logic that the login and su programs go through in validating this password and username. | |||
| impersonating | See spoofing. | |||
| incomplete parameter checking | A system design flaw that results when not all parameters have been fully anticipated for accuracy and consistency, thus making the system vulnerable to penetration. | |||
| individual accountability | The ability to associate positively the identity of a user with the time, method, and degree of access to a system. | |||
| information flow control | A procedure to ensure that information transfers within a system are not made from a higher security level object to an object of a lower security level. See covert channel, simple security property, and star property (*-property). Synonymous with data flow control. | |||
| Information Systems Security Products and Services Catalogue | A catalogue issued quarterly by the National Security Agency that incorporates the DPL, EPL, ETL, PPL and other security product and service lists. This catalogue is available through the U.S. Government Printing Office, Washington, DC (202) 1202) 783-3238. | |||
| instance | The name often given to the second component of a principal identifier, or a particular principal from a group of related principals. In the latter usage, the instances are often created to partition permission for users. For example, a user might have a “normal” instance and a “root” instance (which has different privileges) to impose a naming convention on service key names. For an example of a particular service, the instances identifies the host machines on which that service is provided and the principal identifier of the server. | |||
| integrity | In secure systems, the term “integrity” refers to the relative level of trust a user can place in using a system resource. A program obtained from a public-access bulletin board is of much lower integrity than one purchased from a reputable vendor. This program is in turn of much lower integrity than a program shipped as part of a trusted system. See Mandatory Integrity. Alternatively, sound, unimpaired, or perfect condition. | |||
| integrity label-- MINT | One half of the MAC label. Represents the measure of trust a user can put in a system resource. See MSEN and sensitivity label. | |||
| interdiction | See denial of service. | |||
| internal security controls | Hardware, firmware, and software features within a system that restrict access to resources (hardware, software, and data) to authorized subjects only (persons, programs, or devices). | |||
| isolation | The containment of subjects and objects in a system in such a way that they are separated from one another, as well as from the protection controls of the operating system. | |||
| lattice | A partially ordered set for which every pair of elements has a greatest lower bound and a least upper bound. | |||
| least privilege | The principle that requires that each subject be granted the most restrictive set of privileges needed for the performance of authorized tasks. The application of this principle limits the damage that can result from accident, error, or unauthorized use. | |||
| limited access | See access control. | |||
| lock-and-key protection system | A protection system that involves matching a key or password with a specific access requirement. | |||
| logic bomb | A resident computer program that triggers the perpetration of an unauthorized act when particular states of the system are realized. | |||
| login-spoofing program | This term refers to any program that represents itself as a login program in order to steal your password. For example, a spoofing program might print the UNIX login banner on an unattended system and wait for input from the user. The user dutifully types in the user name, and the program prompts for the password, turning off character echo. After storing away the user's password, the program reports that the password is incorrect and exits, which causes the real login program to be started on the system. The user then logs in, mistakenly assuming that he or she previously mistyped the name or password, and starts a session. | |||
| loophole | An error of omission or oversight in software or hardware that permits circumventing the system security policy. | |||
| MAC | Mandatory Access Control. See Mandatory Access Control. | |||
| MAC label | A MAC label is comprised of two halves: the sensitivity label (MSEN) and the integrity label (MINT). A typical MAC label would be msenhigh/mintlow. This would represent an object with a highly sensitive topic, but with a relatively low level of integrity (perhaps obtained from a questionable source). | |||
| magnetic remanence | A measure of the magnetic flux density remaining after removal of the applied magnetic force. Refers to any data remaining on magnetic storage media after removal of the power. | |||
| maintenance hook | Special instructions in software to allow easy maintenance and additional feature development. These are not clearly defined during access for design specification. Hooks frequently allow entry into the code at unusual points or without the usual checks, so they are a serious security risk if they are not removed before live implementation. Maintenance hooks are special types of trap doors. | |||
| malicious logic | Hardware, software, or firmware that is intentionally included in a system for an unauthorized purpose; for example, a Trojan Horse virus. | |||
| Mandatory Access Control | MAC is a means of restricting access to objects based on the sensitivity and integrity (as represented by a label) of the information contained in the objects and the formal authorization (that is, clearance) of subjects to access information of such sensitivity and integrity. See also Discretionary Access Control. | |||
| Mandatory Integrity | A means of restricting access to objects based on the integrity (as represented by a label) of the information contained in the objects and the subjects. Integrity is necessary to identify the Trusted IRIX/CMW TCB. In order to do so, some mechanism for restricting what programs may be executed by the superuser, auditor, and any other trusted users must be implemented. The Mandatory Integrity (MINT) component of the security label provides TCB isolation by denying access to programs that have not been sufficiently analyzed (or have been and are deemed untrustworthy to users with high integrity requirements). The MINT mechanism allows only those processes whose integrity labels are dominated by an object read or execute access to it. Additionally, a process may write only to an object with the same integrity. The MINT mechanism is very similar to the MSEN mechanism in having 256 hierarchical levels (the grades) and 65,536 non-hierarchical components (the divisions). | |||
| Mandatory Sensitivity | The label of every subject and object on the system indicates a level of security clearance. Access to an object by a subject is based on their relative levels of clearance. A user will not even be aware of the existence of objects that are at a higher level of sensitivity. A sensitivity label (MSEN) is comprised of a type (for example, msenhigh) and a category (for example, Politics, Sports). | |||
| masquerading | See spoofing. | |||
| mimicking | See spoofing. | |||
| MINT | Mandatory Integrity. See Mandatory Integrity. | |||
| multilevel device | A device that is used in a manner that permits it to simultaneously process data of two or more security levels without risk of compromise. To accomplish this, sensitivity labels are normally stored on the same physical medium and in the same form (that is, machine-readable or human-readable) as the data being processed. | |||
| multilevel secure | A class of system containing information with different sensitivities that simultaneously permits access by users with different security clearances and needs-to-know, but prevents users from obtaining access to information for which they lack authorization. | |||
| multilevel security mode | See modes of operation. | |||
| multiple access rights terminal | A system or port that may be used by more than one class of users; for example, users with different access rights to data. | |||
| multiuser mode of operation | A mode of operation designed for systems that process sensitive unclassified information in which users may not have a need-to-know for all information processed in the system. This mode is also for microcomputers processing sensitive unclassified information that cannot meet the requirements of the stand-alone mode of operation. | |||
| mutually suspicious | The state that exists between interacting processes (subsystems or programs) in which neither process can expect the other process to function securely with respect to some property. | |||
| National Computer Security Center | Originally named the DoD Computer Security Center, the NCSC is responsible for encouraging the widespread availability of trusted computer systems throughout the Federal Government. | |||
| National Security Decision Directive 145 | Signed by President Reagan on 17 September 1984, this directive is entitled “National Policy on Telecommunications and Automated Information Systems Security.” It provides initial objectives, policies, and an organizational structure to guide the conduct of national activities toward safeguarding systems that process, store, or communicate sensitive information; establishes a mechanism for policy development; and assigns implementation responsibilities. | |||
| National Telecommunications and Information System Security Directives | NTISS Directives establish national-level decisions relating to NTISS policies, plans, programs, systems, or organizational delegations of authority. NTISSDs are promulgated by the Executive Agent of the Government for Telecommunications and Information Systems Security, or by the Chairman of the NTISSC when so delegated by the Executive Agent. NTISSDs are binding upon all federal departments and agencies. | |||
| National Telecommunications and Information Systems Security Advisory | Memoranda Instructions NTISS Advisory Memoranda and Instructions provide advice, assistance, or information of general interest on telecommunications and systems security to all applicable federal departments and agencies. NTISSAMs/NTISSIs are promulgated by the National Manager for Telecommunications and Automated Information Systems Security and are recommendatory. | |||
| NCSC | National Computer Security Center. | |||
| need-to-know | The necessity for access to, knowledge of, or possession of specific information required to carry out official duties. | |||
| network front end | A device that implements the necessary network protocols, including security-related protocols, to allow a computer system to be attached to a network. | |||
| NSDD 145 | See National Security Decision Directive 145. | |||
| NTISSC | National Telecommunications and Information Systems | |||
| object | A passive entity that contains or receives information. Access to an object potentially implies access to the information it contains. Examples of objects are: records, blocks, pages, segments, files, directories, directory trees, and programs, as well as bits, bytes, words, fields, processors, video displays, keyboards, clocks, printers, and network nodes. | |||
| object reuse | The reassignment and reuse of a storage medium (for example, page frame, disk sector, magnetic tape) that once contained one or more objects. To be securely reused and assigned to a new subject, storage media must contain no residual data (magnetic remanence) from the object(s) previously contained in the media. | |||
| open security environment | An environment that includes those systems in which at least one of the following conditions holds true: (1) Application developers (including maintainers) do not have sufficient clearance or authorization to provide an acceptable presumption that they have not introduced malicious logic. (2) Configuration control does not provide sufficient assurance that applications are protected against the introduction of malicious logic prior to and during the operation of system applications. | |||
| Operations Security | An analytical process by which the U.S. Government and its supporting contractors can deny to potential adversaries information about capabilities and intentions by identifying, controlling, and protecting evidence of the planning and execution of sensitive activities and operations. | |||
| OPSEC | Operations Security. See Operations Security. | |||
| Orange Book | Alternate name for DoD Trusted Computer Security Evaluation Criteria. | |||
| output | Information that has been exported by a TCB. | |||
| overt channel | A path within a computer system or network that is designed for the authorized transfer of data. See also covert channel. | |||
| overwrite procedure | A stimulation to change the state of a bit followed by a known pattern. See also magnetic remanence. | |||
| password | A protected, private character string used to authenticate an identity. | |||
| password aging | An administrator can set a minimum and a maximum amount of time for the use of a given password. A user can be unable to log in if the password had expired and the user ignored warnings to change it. | |||
| penetration signature | The characteristics or identifying marks that may be produced by a penetration. | |||
| penetration study | A study to determine the feasibility and methods for defeating controls of a system. | |||
| penetration testing | The portion of security testing in which the evaluators attempt to circumvent the security features of a system. The evaluators may be assumed to use all system design and implementation documentation, which may include listings of system source code, manuals, and circuit diagrams. The evaluators work under the same constraints applied to ordinary users. | |||
| periods processing | The processing of various levels of sensitive information at distinctly different times. Under periods processing, the system must be purged of all information from one processing period before transitioning to the next when there are different users with differing authorizations. | |||
| permissions | A description of the type of authorized interactions a subject can have with an object. Examples include read, write, execute, add, modify, and delete. | |||
| personnel security | The procedures established to ensure that all personnel who have access to sensitive information have the required authority as well as appropriate clearances. | |||
| physical security | The application of physical barriers and control procedures as preventive measures or countermeasures against threats to resources and sensitive information. | |||
| piggyback | Gaining unauthorized access to a system via another user's legitimate connection. See between-the-lines entry. | |||
| plaintext | The input to an encryption function or the output of a decryption function. Decryption transforms ciphertext into plaintext. | |||
| Preferred Products List | A list of commercially produced equipments that meet requirements prescribed by the National Security Agency. This list is included in the NSA Information Systems Security Products and Services Catalogue, issued quarterly and available through the Government Printing Office. | |||
| principal | A uniquely named client or server instance that participates in a network communication. | |||
| principal identifier | The name used to uniquely identify each different principal. | |||
| print suppression | Eliminating the displaying of characters in order to preserve their secrecy; for example, not displaying the characters of a password as it is keyed in. | |||
| privileged instructions | A set of instructions (for example, interrupt handling or special computer instructions) to control features (such as storage protection features) that are generally executable only when the automated system is operating in the executive state. | |||
| procedural security | See administrative security. | |||
| process | A program in execution. It is completely characterized by a single current execution point (represented by the machine state) and address space. | |||
| protection-critical portions of the TCB | Those portions of the TCB whose normal function is to deal with the control of access between subjects and objects. Their correct operation is essential to the protection of the data on the system. | |||
| protection philosophy | An informal description of the overall design of a system that delineates each of the protection mechanisms employed. A combination, appropriate to the evaluation class, of formal and informal techniques is used to show that the mechanisms are adequate to enforce the security policy. | |||
| protection ring | One of a hierarchy of privileged modes of a system that gives certain access rights to user programs and processes authorized to operate in a given mode. | |||
| protocols | A set of rules and formats, semantic and syntactic, that permits entities to exchange information. | |||
| pseudo-flaw | An apparent loophole deliberately implanted in an operating system program as a trap for intruders. | |||
| Public Law 100-235 | Also known as the Computer Security Act of 1987, this law creates a means for establishing minimum acceptable security practices for improving the security and privacy of sensitive information in federal computer systems. This law assigns to the National Institute of Standards and Technology responsibility for developing standards and guidelines for federal computer systems processing unclassified data. The law also requires establishment of security plans by all operators of federal computer systems that contain sensitive information. | |||
| rainbow series | The informal name given to a set of books published by the NCSC that deal with computer security. The books are published with covers in different colors, hence the term “rainbow.” The most used book in the rainbow series is the Orange Book, the DoD Trusted Computer System Evaluation Criteria. | |||
| read | A fundamental operation that results only in the flow of information from an object to a subject. | |||
| read access | Permission to read information. | |||
| recovery procedures | The actions necessary to restore a system's computational capability and data files after a system failure. | |||
| reference monitor concept | An access-control concept that refers to an abstract machine that mediates all accesses to objects by subjects. | |||
| reference validation mechanism | An implementation of the reference monitor concept. A security kernel is a type of reference validation mechanism. | |||
| reliability | The probability of a given system performing its mission adequately for a specified period of time under the expected operating conditions. | |||
| residual risk | The portion of risk that remains after security measures have been applied. | |||
| residue | Data left in storage after processing operations are complete, but before degaussing or rewriting has taken place. | |||
| resource encapsulation | The process of ensuring that a resource not be directly accessible by a subject, but that it be protected so that the reference monitor can properly mediate accesses to it. | |||
| restricted area | Any area to which access is subject to special restrictions or controls for reasons of security or safeguarding of property or material. | |||
| risk | The probability that a particular threat will exploit a particular vulnerability of the system. | |||
| risk analysis | The process of identifying security risks, determining their magnitude, and identifying areas needing safeguards. Risk analysis is a part of risk management. Synonymous with risk assessment. | |||
| risk assessment | See risk analysis. | |||
| risk index | The disparity between the minimum clearance or authorization of system users and the maximum sensitivity (for example, classification and categories) of data processed by a system. | |||
| risk management | The total process of identifying, controlling, and eliminating or minimizing uncertain events that may affect system resources. It includes risk analysis, cost benefit analysis, selection, implementation and test, security evaluation of safeguards, and overall security review. | |||
| RM Plan | The Rating Maintenance Plan (RM-Plan) is a living document that describes the policies which govern modifications to the Trusted IRIX/CMW system and the procedures used to implement these policies. It describes in detail the initial contents of the system, and how each component of the Trusted Computing Base was approved for inclusion. The procedures for making changes to the system for future releases are defined. The change request mechanisms for new features, performance enhancements, and field-detected security failures are described. The methods by which changes are tracked are defined in the RM-Plan. Source code control, document control, the product naming scheme, and methods for identification of changes to the RM-Plan itself are described. Evidence supporting the validity and necessity of changes is maintained. | |||
| safeguards | See security safeguards. | |||
| scavenging | Searching through object residue to acquire unauthorized data. | |||
| seal | To encipher a record containing several fields in such a way that the fields cannot be individually replaced without either knowledge of the encryption key or leaving evidence of tampering. | |||
| secure configuration management | The set of procedures appropriate for controlling changes to a system's hardware and software structure for the purpose of ensuring that changes will not lead to violations of the system's security policy. | |||
| secure state | A condition in which no subject can access any object in an unauthorized manner. | |||
| secure subsystem | A subsystem that contains its own implementation of the reference monitor concept for those resources it controls. However, the secure subsystem must depend on other controls and the base operating system for the control of subjects and the more primitive system objects. | |||
| Security Administration Guide | This document describes the administration of the security features of Trusted IRIX/CMW. Instructions are provided on planning and administering a trusted system, managing Mandatory Access Control, Auditing, and Identification and Authentication facilities. Also, the document covers printing and use of magnetic media in a trusted environment. The NCSC requires this document as part of the evaluation materials. The NCSC name for this kind of document is a “Trusted Facilities Manual.” The Trusted IRIX/CMW Security Administrator's Guide is the Trusted Facilities Manual for Trusted IRIX/CMW. | |||
| security critical mechanisms | Those security mechanisms whose correct operation is necessary to ensure that the security policy is enforced. | |||
| security evaluation | An evaluation done to assess the degree of trust that can be placed in systems for the secure handling of sensitive information. One type, a product evaluation, is an evaluation performed on the hardware and software features and assurances of a computer product from a perspective that excludes the application environment. The other type, a system evaluation, is done for the purpose of assessing a system's security safeguards with respect to a specific operational mission and is a major step in the certification and accreditation process. | |||
| security fault analysis | A security analysis, usually performed on hardware at gate level, to determine the security properties of a device when a hardware fault is encountered. | |||
| security features | The security-relevant functions, mechanisms, and characteristics of system hardware and software. Security features are a subset of system security safeguards. | |||
| Security Features User's Guide | This document exists to describe in layman's terms the user visible portion of the security features of the Trusted IRIX/CMW operating system. This book describes for the user specific methods for effectively using the system. It also describes what the user is not allowed to do and what actions the user should take when faced with a denial of service. | |||
| security filter | A trusted subsystem that enforces a security policy on the data that pass through it. | |||
| security flaw | An error of commission or omission in a system that may allow protection mechanisms to be bypassed. | |||
| security flow analysis | A security analysis performed on a formal system specification that locates potential flows of information within the system. | |||
| security kernel | The hardware, firmware, and software elements of a TCB that implement the reference monitor concept. It must mediate all accesses, be protected from modification, and be verifiable as correct. | |||
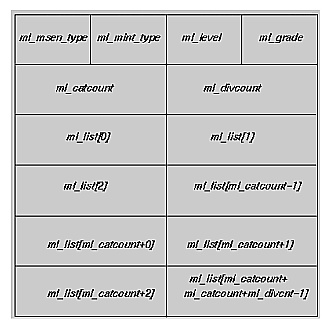
| security label | The data structure used to associate a security clearance or classification to each subject and object in Trusted IRIX/CMW. The structure of a security label is shown in Figure A-1. | |||
| security measures | Elements of software, firmware, hardware, or procedures that are included in a system for the satisfaction of security specifications. | |||
| security perimeter | The boundary where security controls are in effect to protect assets. | |||
| security policy | The set of laws, rules, and practices that regulate how an organization manages, protects, and distributes sensitive information. | |||
| security policy model | A formal presentation of the security policy enforced by the system. It must identify the set of rules and practices that regulate how a system manages, protects, and distributes sensitive information. See Bell-La Padula model and formal security policy model. | |||
| security range | The highest and lowest security levels that are permitted in or on a system, system component, subsystem, or network. | |||
| security requirements | The types and levels of protection necessary for equipment, data, information, applications, and facilities to meet security policy. | |||
| security requirements baseline | A description of minimum requirements necessary for a system to maintain an acceptable level of security. | |||
| security safeguards | The protective measures and controls that are prescribed to meet the security requirements specified for a system. Those safeguards may include but are not necessarily limited to hardware and software security features, operating procedures, accountability procedures, access and distribution controls, management constraints, personnel security, and physical structures, areas, and devices. Also called safeguards. | |||
| security specifications | A detailed description of the safeguards required to protect a system. | |||
| security test and evaluation | An examination and analysis of the security safeguards of a system as they have been applied in an operational environment to determine the security posture of the system. | |||
| security testing | A process used to determine that the security features of a system are implemented as desired. This includes hands-on functional testing, penetration testing, and verification. | |||
| sensitive information | Any information, whose loss, misuse, modification of, or unauthorized access to, could affect the national interest or the conduct of Federal programs, or the privacy to which individuals are entitled under Section 552a of Title 5, U.S. Code, but that has not been specifically authorized under criteria established by an Executive order or an act of Congress to be kept classified in the interest of national defense or foreign policy. | |||
| sensitivity | In secure systems, sensitivity is a measure of the risk associated with the disclosure of the data in question. A map of a foreign city (UNCLASSIFIED) is less sensitive than the map of a foreign military base (SECRET) which is in turn less sensitive than the name of the asset who provided the maps (TOP SECRET). | |||
| sensitivity label | One half of the MAC label. Where the MINT half represents the degree of confidence a user may have in the integrity of a system resource, the sensitivity label is a relative representation of the degree of risk associated with the disclosure of the data in question. Sensitivity labels are used by the TCB as the basis for mandatory access control decisions. | |||
| sensitivity level | The sensitivity level is the hierarchical portion of the sensitivity label. See sensitivity label. | |||
| server | A particular Principal that provides a resource to network clients. | |||
| service | A resource provided to network clients; often provided by more than one server (for example, remote file service). | |||
| session key | A temporary encryption key used between two principals, with a lifetime limited to the duration of a single communications “session. | |||
| SFUG | See Security Features User's Guide. | |||
| simple security condition | See simple security property. | |||
| simple security property | A Bell-La Padula security model rule allowing a subject read access to an object only if the security level of the subject dominates the security level of the object. Synonymous with simple security condition. | |||
| single-level device | An automated information systems device that is used to process data of a single security level at any one time. Because the device need not be trusted to separate data of different security levels, sensitivity labels do not have to be stored with the data being processed. | |||
| software security | General purpose (executive, utility or software development tools) and applications programs or routines that protect data handled by a system. | |||
| software system test and evaluation process | A process that plans, develops and documents the quantitative demonstration of the fulfillment of all baseline functional performance, operational, and interface requirements. | |||
| spoofing | An attempt to gain access to a system by posing as an authorized user. Synonymous with impersonating, masquerading or mimicking. | |||
| stand-alone shared system | A system that is physically and electrically isolated from all other systems, and is intended to be used by more than one person, either simultaneously (for example, a system with multiple monitors) or serially, with data belonging to one user remaining available to the system while another user is using the system (for example, a personal computer with nonremovable storage media such as a hard disk). | |||
| stand-alone single-user system | A system that is physically and electrically isolated from all other systems, and is intended to be used by one person at a time, with no data belonging to other users remaining in the system (for example, a personal computer with removable storage media such as a floppy disk). | |||
| star property | See *-property. | |||
| state variable | A variable that represents either the state of the system or the state of some system resource. | |||
| storage object | An object that supports both read and write accesses. | |||
| STS | Subcommittee on Telecommunications Security of NTISSC | |||
| Subcommittee on Automated Information Systems Security | NSDD-l 45 authorizes and directs the establishment, under the NTISSC, of a permanent Subcommittee on Automated Information Systems Security. The SAISS is composed of one voting member from each organization represented on the NTISSC. | |||
| Subcommittee on Telecommunications Security | NSDD-145 authorizes and directs the establishment, under the NTISSC, of a permanent Subcommittee on Telecommunications Security. The STS is composed of one voting member from each organization represented on the NTISSC. | |||
| subject | An active entity, generally in the form of a person, process, or device, that causes information to flow among objects or changes the system state. Technically, a process/domain pair. | |||
| subject security level | A subject's security level is equal to the security level of the objects to which it has both read and write access. A subject's security level must always be dominated by the clearance of the user with which the subject is associated. | |||
| supervisor state | See executive state. | |||
| System Call Security Analysis | A document that describes the security policies, both discretionary and mandatory, enforced by each of the Trusted IRIX/CMW system calls. For each system call the differences in behavior between the superuser and normal users, if any, are described. The object reuse policies are discussed. This document is the heart of the security policy description in that it describes which interfaces to the Trusted Computing Base are affected and implement the system security policy. It is explicit and definitive. | |||
| system integrity | The quality that a system has when it performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system. | |||
| system low | The lowest security level supported by a system at a particular time or in a particular environment. | |||
| Systems Security Steering Group | The senior government body established by NSDD-145 to provide top-level review and policy guidance for the telecommunications security and automated information systems security activities of the U.S. Government. This group is chaired by the Assistant to the President for National Security Affairs and consists of the Secretary of State, Secretary of Treasury, the Secretary of Defense, the Attorney General, the Director of the Office of Management and Budget, and the Director of Central Intelligence. | |||
| tampering | An unauthorized modification that alters the proper functioning of a piece of equipment or system in a manner that degrades the security or functionality it provides. | |||
| TCB | Trusted Computing Base. See Trusted Computing Base. | |||
| TCSEC | DoD Trusted Computer System Evaluation Criteria. | |||
| technical attack | An attack that can be perpetrated by circumventing or nullifying hardware and software protection mechanisms, rather than by subverting system personnel or other users. | |||
| technical vulnerability | A hardware, firmware, communication, or software flaw that leaves a computer processing system open for potential exploitation, either externally or internally, thereby resulting in risk for the owner, user, or manager of the system. | |||
| Test Plan | A single document describes the overall planning for testing Trusted IRIX/CMW. This document discusses the documentation plan for testing, the design goal, software requirements, general testing requirements, testing strategies, approaches, methods, hardware resources, software resources, personnel resources, schedules, and milestones. | |||
| TFM | Trusted Facilities Manual. See also Security Administration Guide. | |||
| threat | Any circumstance or event with the potential to cause harm to a system in the form of destruction, disclosure, modification of data, and/or denial of service. | |||
| threat agent | A method used to exploit a vulnerability in a system, operation, or facility. | |||
| threat analysis | The examination of all actions and events that might adversely affect a system or operation. | |||
| threat monitoring | The analysis, assessment, and review of audit trails and other data collected for the purpose of searching out system events that may constitute violations or attempted violations of system security. | |||
| time-dependent password | A password that is valid only at a certain time of day or during a specified interval of time. | |||
| top-level specification | A nonprocedural description of system behavior at the most abstract level; typically, a functional specification that omits all implementation details. | |||
| trap door | A hidden software or hardware mechanism that can be triggered to permit system protection mechanisms to be circumvented. It is activated in some innocent-appearing manner; for example, a special “random” key sequence at a monitor. Software developers often introduce trap doors in their code to enable them to reenter the system and perform certain functions. Synonymous with back door. | |||
| Trojan Horse | A computer program with an apparently or actually useful function that contains additional (hidden) functions that surreptitiously exploit the legitimate authorizations of the invoking process to the detriment of security. For example, making a “blind copy” of a sensitive file for the creator of the Trojan Horse. | |||
| trusted computer system | A system that employs sufficient hardware and software assurance measures to allow its use for simultaneous processing of a range of sensitive or classified information. A system is trusted when it is believed that it can enforce a particular security policy. A CMW level of trust will provide the user and administrator of a system with a given level of trust in its ability to protect data from disclosure. | |||
| Trusted Computing Base | The totality of protection mechanisms within a computer system, including hardware, firmware, and software, the combination of which is responsible for enforcing a security policy. A TCB consists of one or more components that together enforce a unified security policy over a product or system. The ability of a TCB to enforce correctly a unified security policy depends solely on the mechanisms within the TCB and on the correct input by system administrative personnel of parameters (for example, a user's clearance level) related to the security policy. Alternatively, this term refers to the set of hardware and software that together enforce the system's security policy. The TCB comprises only those programs and hardware elements that are known to follow security policy and are considered to be secure. This is necessarily a subset of all the programs available with Trusted IRIX/CMW. | |||
| trusted distribution | A trusted method for distributing the TCB hardware, software, and firmware components, both originals and updates, that protects the TCB from modification during distribution and detects any changes to the TCB that may occur. | |||
| Trusted IRIX/B | The trademarked name for the trusted operating system that preceded Trusted IRIX/CMW | |||
| Trusted IRIX/CMW | The trademarked name (Trusted IRIX/CMW) for the trusted version of IRIX at the B1/CMW level. | |||
| trusted path | A mechanism by which a person at a system can communicate directly with the TCB. This mechanism can only be activated by the person or the TCB and cannot be imitated by untrusted software. | |||
| trusted process | A process whose incorrect or malicious execution is capable of violating system security policy. | |||
| trusted software | The software portion of the TCB. | |||
| untrusted process | A process that has not been evaluated or examined for adherence to the security policy. It may include incorrect or malicious code that attempts to circumvent the security mechanisms. | |||
| user | Person or process accessing the system either by direct connections (that is, via the system console), or indirect connections (that is, prepare input data or receive output that is not reviewed for content or classification by a responsible individual). | |||
| user ID | A unique symbol or character string that is used by a system to identify a specific user. | |||
| user profile | Patterns of a user's activity that can be used to detect changes in normal routines. | |||
| virus | A self-propagating Trojan horse, composed of a mission component, a trigger component, and a self-propagating component. | |||
| vulnerability | A weakness in system security procedures, system design, implementation, internal controls, and so on, that could be exploited to violate system security policy. | |||
| vulnerability analysis | The systematic examination of systems in order to determine the adequacy of security measures, identify security deficiencies, and provide data from which to predict the effectiveness of proposed security measures. | |||
| vulnerability assessment | A measurement of vulnerability that includes the susceptibility of a particular system to a specific attack and the opportunities available to a threat agent to mount that attack. | |||
| work factor | An estimate of the effort or time needed by a potential penetrator with specified expertise and resources to overcome a protective measure. | |||
| worm | A virus program that has a very narrow purpose. A worm is designed to track down and eliminate specific data. Unlike a simple virus, which by its very nature is obviously present, a worm is designed to remain unnoticed in order that it may continue its task unchecked. Because it may follow a serpentine path in its hunt for particular data it has earned the nickname “worm.” | |||
| write | A fundamental operation that results only in the flow of information from a subject to an object. | |||
| write access | Permission to write to an object. |